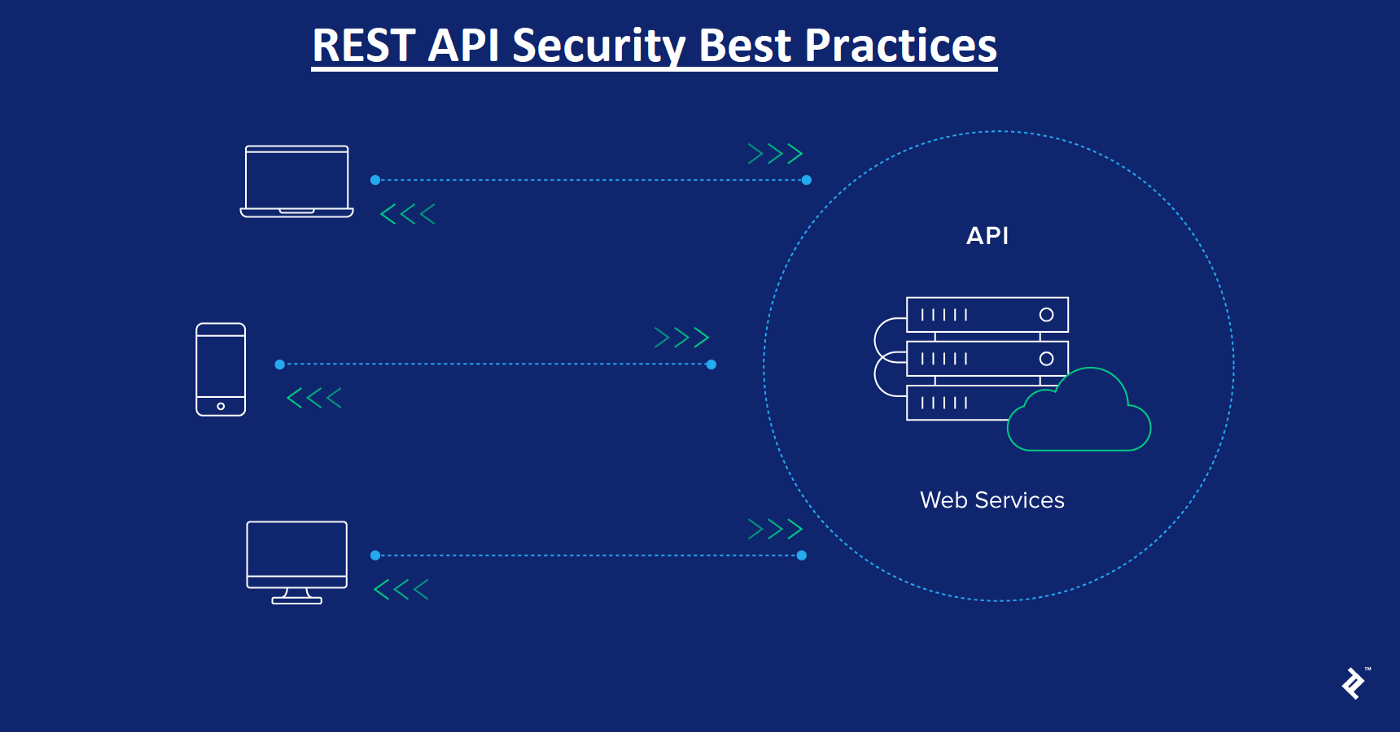
You ought to never underestimate API security. Associations have opened up their environment through REST APIs because of the rising requirement for information driven projects. Accordingly, you want to know how to safeguard public REST APIs.
They are the passageways to an organization’s exceptionally safeguarded information. Moreover, public APIs empower correspondence between numerous applications.
There are several ways to protect your public rest APIs. These include encryption, limiting the scope and type of requests, throttling limits and quotas, and function level authorization. Let’s take a look at a few of them. These measures are necessary for any public rest API to avoid being compromised by hackers.
By all accounts, this seems, by all accounts, to be phenomenal in light of the fact that it improves on engineers’ lives, however it represents a problem. Keeping the API environment’s entryways open while keeping programmers out is testing. Notwithstanding, there are ways you can make it happen and systems that you can utilize to receive the rewards that APIs offer while guarding every one of your information. This article will show you how to securely safeguard public REST APIs and utilize the APILayer commercial center.
Why Is API Security Important?
Because of their open availability, APIs are regularly utilized as focuses for the burglary of touchy information, including application rationale, client accreditations, and charge card subtleties. We should discuss a few API shortcomings.
Since multifaceted validation and logins utilizing certifications are once in a while seen as impossible for API calls, fundamental verification represents a unique trouble for APIs. APIs with unfortunate confirmation, for example, erroneous access token execution, empower programmers to claim to be approved clients since APIs depend on meeting tokens encoded in the calls to verify clients. On the opposite side, diligent tokens additionally permit aggressors to proceed, forever compromising the framework.
Expected Threats
Object-level consent in APIs is a code-level control to check object access. An outside client can supplant the ID of their asset with the ID of one more client’s asset for APIs with object-level approval defects. By empowering assailants to get to the asset having a place with the assigned client, delicate data might be gotten to without approval.
They could settle on numerous decisions each second in the event that the API doesn’t limit the amount and recurrence of solicitations from a particular client. Also, the API client can get to a few assets and information on the double, over-burdening the application server and expecting it to quickly answer each solicitation. Because of the server’s trouble handling an excessive number of solicitations on the double, this can bring about Denial-of-Service assaults. Furthermore, the shortfall of rate-restricting urges programmers to utilize beast force strategies to go after validation endpoints.
The APIs naturally channel client contribution to items or program factors helpless against a mass task. Albeit this usefulness makes it simpler to compose code, a few clients might introduce and change server-side factors, which could think twice about application. Assailants for the most part exploit this by making reasonable deductions and including different item qualities while making demands. Moreover, they can peruse the application’s documentation or find weak API endpoints that give them admittance to server-side articles.
What Practices Should You Follow To Protect Public Rest APIs?
The weakness of public REST APIs has in this manner been demonstrated. Thus, getting these incorporations has turned into a business-basic errand, particularly taking into account the developing risk of cyberattacks. Luckily, API suppliers can forestall numerous potential dangers by sticking to a couple of essential practices.
Encrypting requests and responses to prevent MITM attacks
The most basic way to prevent MITM attacks is by encrypting your requests and responses. The reason is simple: if your API is not secured with TLS, an attacker could intercept communications and steal confidential information. These attacks are widespread and can target any industry.
HTTP requests generated by browsers typically contain a Referer header, which contains the URL of the page that generated the request. This means that any sensitive information contained in a GET request could end up in a subsequent request’s Referer header. By contrast, POST requests don’t contain this problem.
This attack takes advantage of the fact that most web applications generate a temporary session token to identify the user and make subsequent requests. This session token can be sniffed by an attacker, and it doesn’t even require spoofing to do so. Once an attacker has obtained a session token, they can make requests and use this information to steal sensitive information. Another common attack method is SSL stripping, where an attacker intercepts traffic and forces a host to make unencrypted requests, exposing sensitive information in plain text.
The man-in-the-middle attack occurs when an unauthorized person intercepts communication between two parties and alters it for financial or disruption purposes. MITM attacks come in many forms and exploit various weaknesses in security practices. For example, an attacker may pretend to be the person who is sending the message while listening to the conversation. They can even pose as an official source and intercept sensitive information, or even make it look legitimate.
Protect Public REST APIs Using HTTPS/TLS
HTTPS and Transport Layer Security (TLS) give a safe convention to convey encoded information between internet browsers and servers. Alongside safeguarding different sorts of information, HTTPS additionally supports getting login certifications while they are communicated. Each apus ought to involve HTTPS as one of the main practices to guarantee honesty, secrecy, and validness. Security groups ought to likewise consider embracing client-side commonly confirmed declarations, which offer extra security for basic data and administrations. Engineers ought to abstain from changing HTTP to HTTPS while making a protected REST API, as this could think twice about client security. CORS and JSONP inquiries ought to be redirected fittingly because of their innate cross-area call weaknesses.
Encrypting requests and responses to prevent MITM attacks
The most basic way to prevent MITM attacks is by encrypting your requests and responses. The reason is simple: if your API is not secured with TLS, an attacker could intercept communications and steal confidential information. These attacks are widespread and can target any industry.
HTTP requests generated by browsers typically contain a Referer header, which contains the URL of the page that generated the request. This means that any sensitive information contained in a GET request could end up in a subsequent request’s Referer header. By contrast, POST requests don’t contain this problem.
This attack takes advantage of the fact that most web applications generate a temporary session token to identify the user and make subsequent requests. This session token can be sniffed by an attacker, and it doesn’t even require spoofing to do so. Once an attacker has obtained a session token, they can make requests and use this information to steal sensitive information. Another common attack method is SSL stripping, where an attacker intercepts traffic and forces a host to make unencrypted requests, exposing sensitive information in plain text.
The man-in-the-middle attack occurs when an unauthorized person intercepts communication between two parties and alters it for financial or disruption purposes. MITM attacks come in many forms and exploit various weaknesses in security practices. For example, an attacker may pretend to be the person who is sending the message while listening to the conversation. They can even pose as an official source and intercept sensitive information, or even make it look legitimate.
Restricting the type and scope of requests
You can restrict the type and scope of requests made to your public REST APIs using HTTP security headers. Specifically, you should use CORS and X-Content-Type-Options headers to limit the types of requests your APIs can receive. By limiting the request size and content, you can prevent attacks such as cross-site scripting and clickjacking. In addition, you should also make sure that the API parameters are strong-typed.
One way to limit the number of requests made to your REST API is to implement pagination. Pagination allows your APIs to limit their results by page, i.e. the number of records in a single page. You can also use the limit parameter to set a custom page size. But note that not all APIs respect pagination. For instance, you may not be able to limit the number of assets you return per request.
Using consent screens is another way to restrict the types of requests made to public APIs. For instance, if you use API calls to create a customer database, you will likely need to grant access to certain users. The scopes granted will be part of the access token sent to the API. In this way, you can control how much information your application can access.
By restricting the types and scope of API requests, you can ensure that your API will remain secure. In addition, it will prevent any malicious attacks or DoS attacks. By setting restrictions for your public rest APIs, you can protect your public API from unwanted users.
Throttling limits and quotas
Throttling limits and quotas are two ways to control the amount of requests an API can handle at one time. Rate limits are used to prevent an API from sustaining a high usage rate, while quotas allow a high amount of traffic to periodically come to an end. Both rate limits and quotas are effective in controlling API usage, but rate limiting is a better solution for high volume APIs than quotas.
Throttling limits and quotas can also be used to control user authentication and API access. Throttling limits can be set for a certain rate or based on the size of a payload. These limits can be customized to accommodate the needs of varying departments and applications.
Throttling limits and quotas in public rest APIs can be set for the url, method, and endpoint. The LimitRequests attribute limits the number of requests a given endpoint can accept per second. The LimitRequests decorator prevents a third request within five seconds of setting the limit. This feature is important for limiting the amount of traffic an API can handle, and it will limit the number of requests per endpoint.
Rate limits and quotas are useful for protecting the health of a public API. They protect against denial-of-service attacks and slow performance. They also help improve the overall user experience. By limiting the number of requests a given API can handle, the API will be more reliable and more responsive.
Throttling limits and quotas help businesses fight against denial-of-service attacks. These attacks can bring down a website or mobile application by sending enormous volumes of requests. This is why implementing API throttling mechanisms is important. Throttling logic checks whether a request is within the limit and returns an error response if it exceeds the limit.
Function-level authorization
Function-level authorization is an essential part of any REST API security strategy. Without it, an API could be exposed to attackers by accident, allowing access to sensitive data. For example, if a website relies on a credit card API, it could accidentally expose sensitive data. Such an occurrence can lead to denial-of-service attacks or credential stuffing. Thankfully, there are several options to protect public APIs from such abuses.
API developers should follow the principle of least privilege when designing their APIs. This means using predefined roles to oversee user permissions. This makes it more difficult for bad actors to gain access to sensitive data. They should also set up rules for determining which types of API requests are friendly and which are harmful.
APIs should be securely configured to use HTTPS. HTTPS is a standard protocol for communication. Providing security for these APIs is critical for any data-dependent project. Security starts with an understanding of the risks involved, such as a signature-based attack. It also means implementing stricter rules for JSON schemas and paths. Additionally, APIs should be secured by rate limits.
If you have many APIs, you’ll need to implement basic auth to protect them. The Developer Edition of Okta offers most developer features. You can also use its API Access Management product, but it’s not necessary for production environments. You can also use it as a standalone product, or use it as an add-on in your Production environment.
API security is one of the top priorities for security professionals and risk management professionals. Fortunately, there are a number of well-established practices and patterns to protect APIs.
OAuth2
Protecting public rest APIs with OAuth2 requires a few extra steps. For example, it’s important to use scopes to limit the capabilities of Access Tokens. This way, even if client credentials are stolen, the attacker will have less power. In addition, API Gateway verification can help limit malicious traffic.
While OAuth is extensible and flexible, it is not designed to address all scenarios. For instance, some applications might want a more secure authentication mechanism. There are many options when it comes to OAuth, and it’s not necessary to implement them all. There are several RFCs covering the topic.
OAuth security tokens have some limitations, but they are designed to allow end users to place limitations on what they can and cannot access. This means you can set a tiered authorization level to control access to your API. Also, you can set an expiration date for the tokens. This means that if a user tries to access your API without authorization, the token expires after a predefined amount of time.
If you’re building a REST API, you should consider security as an integral part of your development project. Basic auth and OAuth are both secure options, but make sure to use a stateless authentication method that doesn’t rely on sessions. When implementing security, make sure each request is associated with an authentication credential that must be validated on the server. This way, the user experience doesn’t have to suffer.
If you have a web application, you should use an OAuth 2.0 endpoint. You can also include a code, if you want to limit the scope of your API. OAuth 2.0 works with web server applications as well. By integrating OAuth with your API, you can ensure your users’ privacy.
Continuously Use a Gateway
Continuously, our most memorable recommendation is to conceal your API behind a passage. At the point when a solicitation comes into your API, API passages apply incorporated traffic elements to each ask for. For instance, rate limitation, forestalling fake clients, and legitimate logging are a couple of safety related perspectives. Or on the other hand, they may be more valuable and business-related, like revising ways and headers, and gathering business measurements.
A significant security concern might emerge in the event that these techniques weren’t set up. Programming interface suppliers should give these functionalities to every endpoint without an entryway. An API passage makes adding or fixing these functionalities simpler. Luckily, there are numerous API Gateway choices available.
Throttling and Rate Limiting
Choking is regularly utilized as an enemy of spam measure to stop misuse or forswearing of-administration assaults and incorporates setting a transitory express that empowers the API to evaluate each solicitation.
Then again, by forestalling DoS and Brute Force assaults, rate-restricting guides in overseeing REST API security. A few APIs’ engineers give “delicate limitations,” which briefly grant clients to make a greater number of solicitations than permitted. One straightforward API security best practice is setting breaks since it can deal with both coordinated and nonconcurrent inquiries. The improvement of APIs that just acknowledge a specific number of solicitations prior to putting the leftover ones in a holding up line is made conceivable in response to popular demand line libraries. To carry out demand lines, each programming language has a line library catalog.
Reviewing and Managing Your APIs
Regardless of the number of freely open APIs an organization that has, it should initially know about them to get and oversee them. Suddenly, many are not. Work with DevOps groups to deal with your APIs subsequent to leading border outputs to find and stock them.
Can You Follow These Practices While Using APILayer’s APIs?
A commercial center that unites API providers and clients on a solitary stage is known as an API commercial center. There are different parts to an API commercial center, including a supplier and designer entry. Designers or organizations can list their APIs available to be purchased on an API commercial center, where API purchasers (different engineers) can look at and get them.
The API commercial center and administrations of cloud-based SAAS supplier APILayer were presented in February 2022. Brief API, a stage that empowers designers to adapt their APIs, was bought. With over 15 years of mastery making and distributing safe APIs, APILayer is a market chief in the API space.
Every one of the guidelines are maintained by APILayer. Rate impediment is the principal focal point of all APIs on APILayer. Every API has been painstakingly decided to offer the best execution measurements. Furthermore, we can supply devoted cases for bigger establishments.
Passwords are put away in this commercial center utilizing industry-standard non-reversible hashing strategies. Your qualifications are stowed away from representatives of APILayer and some other gatherings.
For more secure correspondence, you can switch among HTTP and HTTPS for any APIs on this market.
What’s the Bottom Line?
Taking everything into account, it’s miserable that there are numerous web-based dangers and that programmers are steady. Nonetheless, safeguarding your information requires areas of strength for a security procedure. Incorporating API security into the general methodology and system of building and creating APIs is a definitive best practice.
Furthermore, coordinate security into the plan cycle from the beginning while at the same time using the proper innovations and a more intentional interaction. Before they appear, security dangers can be found and countered.
The primary worries of APILayer, a painstakingly controlled commercial center for APIs, are dependability, versatility, quality, and security. With only one API key and SDK, it empowers API designers to bring in cash from their APIs while simplifying it for others to make the following extraordinary thing.
- Also Read: Condogames.xyz Roblox Know The Exciting Details!
- Also Read: Saints Row Is Actually Better Than You Have Heard Know Details!